Hacking has always been an attractive topic for me. Around ten years ago, I tried using Kali Linux to try and steal WiFi credentials with aircrack-ng1. However, I had never put much effort into learning or even researching the topic. This changed a month ago when I started my cybersecurity journey at TryHackMe.com. Over the past month, I've learned a lot about Linux, Windows, shells, networking, and web security.
In this post, I'll give a walkthrough of the Pickle Rick room at TryHackMe, which is the final challenge in the Web Hacking Fundamentals module. This was my first-ever attempt at a CTF2, so don't expect this to be a smooth ride. I'll share with you my thought process, the rabbit holes I slipped into, and my frustration until I finally found the correct way.
Pickle Rick
This was the only description of the challenge
This Rick and Morty-themed challenge requires you to exploit a web server and find three ingredients to help Rick make his potion and transform himself back into a human from a pickle.
I deployed the target machine and waited for it to be up.
First steps
The first thing I did after the machine was up was copying its ip address into my /etc/hosts file so I could access it via the target.thm URL. With this set up I went directly to http://target.thm as the description mentions that I have to exploit a web app.
I land on a web page where Rick asks Morty for help accessing his machine. Inspecting the page's source reveals the first hint: a comment where Rick had left a not to himself remembering his username: "R1ckRul3s".
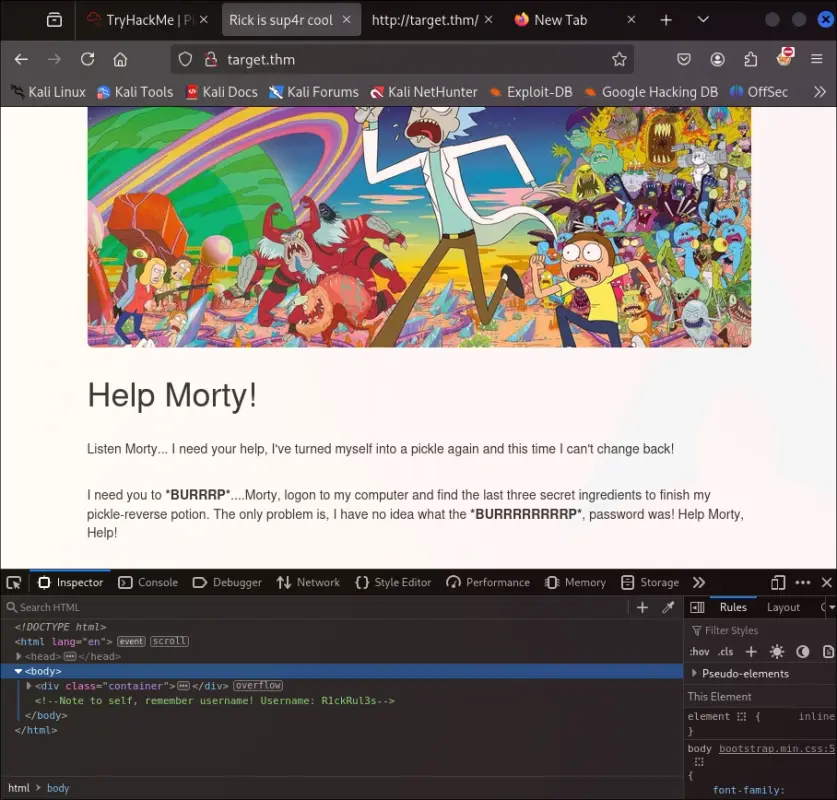
With that information in mind, I went to /login, but there was nothing there, neither at /signup nor /logon. I needed to do some enumeration.
Enumeration
I first ran nmap3 to scan for possible open ports and also started running gobuster4 to enumerate directories in the website. As that was running I tried /robots.txt to check for a disallow section or any other interesting information but I found only one word: Wubbalubbadubdub.
Nmap only returned ports 22 and 80 opened. I tried connecting via ssh with users rick and root, but this didn't work, the server was expecting a key.
Gobuster only found the /assets/ directory, which contained images, jquery.min.js, and Bootstrap JavaScript files, but nothing that hinted at an exploitable vulnerability. I had nothing.
I knew the page was made with php from the headers of the response, so I added the .php and some other extensions to Gobuster and tried enumerating again. In the meantime I downloaded the images from /assets/ and passed them to exiftool5 to check for information there. Nothing.
Credentials discovery
The new gobuster scan revealed a few more interesting directories, like .htaccess [403], portal.php [403], login.php [200]. I already had the username, but I didn't have the password, so I started bruteforcing the login form with hydra6.
Here I spent a lot of time, around one and a half hours, because no wordlist had the password. I continued poking around but didn't find anything. I thought that maybe I should generate my own wordlist with Rick and Morty related stuff like its Wikipedia page, the transcripts of the episodes, or maybe even the contents of the challenge's web page.
With this last thought in mind, I returned to the /robots.txt to grab that word as a candidate, I tried it manually and it worked!
I was both relieved that I finally made some progress and annoyed that I had spent that much time trying to bruteforce the password without trying that before. To me, this seems like something that would not actually happen in a real-world scenario, or at least not very often.
Remote Code Execution
After login, we are redirected to the /portal.php page that contains a "Command Panel", a form that enables us to run commands on the machine, like ls.
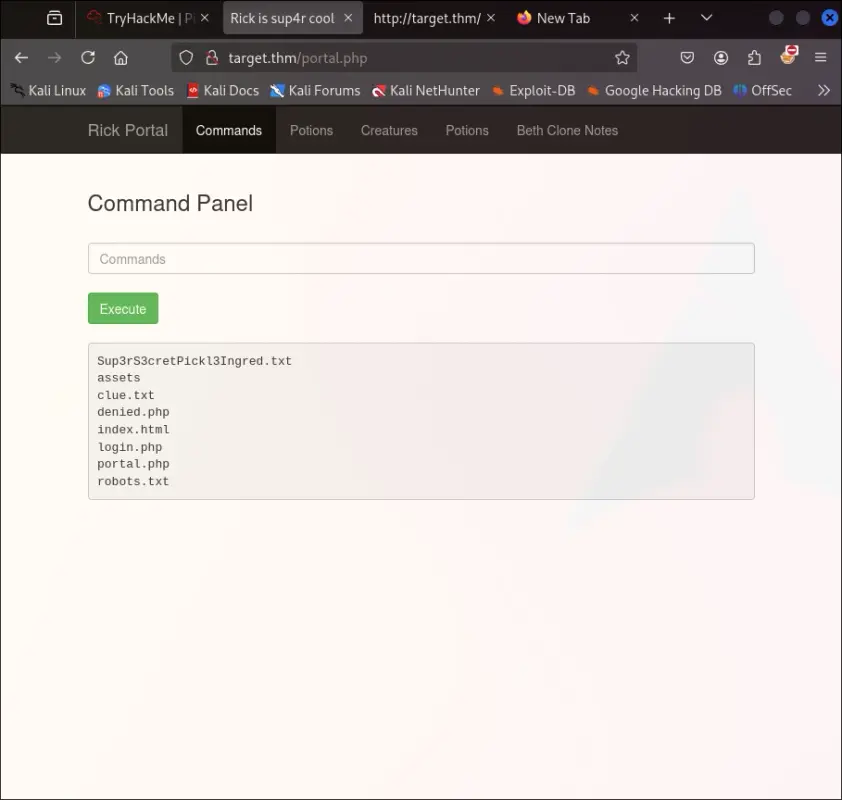
I tried running cat with the files but it wasn't permitted, neither was head or tail. I could, however, navigate to the files with the browser and display them there. There I found the first ingredient and also a clue that told me to continue navigating the filesystem to get the other two.
Reverse shell
Executing commands through that interface was restrictive, so I tried opening a reverse shell. I started listening with Netcat7 at port 9001
.sh
and tried commands from pentestmonkey's Reverse Shell Cheat Sheet. I tried some that didn't work, now I'm not sure if it was just because I didn't update the ip to point to mine or if it was because the machine didn't have python but python3 did. I finally got the reverse shell with php:
.sh
I was in, as www-data, I could cat and move through the filesystem. I found the second ingredient fairly quickly by checking the /home directory. I actually went there to check if I could find any way to access via ssh but found nothing.
Upgrading the shell
Eventually, I upgraded my shell to a better one with
.sh
Privilege escalation
I poked around for a while but didn't find anything new that I had access to. I needed to escalate privileges so I could see what I wasn't seeing. Here again I spent a lot of time, searching on the internet how to do it. I didn't research that well, though. I finally got root access "by accident", I typed sudo su ready to try my best guess against the password, but I didn't need one!
There it was the third ingredient and I finished the challenge!
Lessons learned
Here's a non-exhaustive list of the lessons I learned
- Enumerate! I was stuck with that
/assets/dir for some time because I hadn't found any directory. Adding the file extensions is needed! - Try everything! It did pass through my head that maybe the word in
/robots.txtwas the password from the beginning, had I tried it then it would have spared me a few hours of frustration. - Upgrade to a better shell soon. I spent a lot of time using the first reverse shell I got instead of upgrading to a better one. That's just because I'm new to this, but I'll keep it in mind for the future.
- Always check for the permissions of your user, by running
sudo -l. Had I known that I would have escalated privileges from the beginning and finished the challenge an hour earlier.
Conclusions
This was the last room of the Web Hacking Fundamentals module of TryHackMe. On finishing that I earned a certificate that I'll proudly share with you

This joins the (now) list of certificates of completion from TryHackMe along with Cyber Security 101. You can check my account here to see all my shiny badges and stats.

This was just the first step in my cybersecurity journey, and I can’t wait to tackle even more challenging CTFs. Stay tuned for more write-ups, and remember: think outside the box and stay curious!
Aircrack-ng is a suite of tools for assessing WiFi network security, including password cracking.
Capture the Flag (CTF) in computer security is an exercise in which participants attempt to find text strings, called "flags", which are secretly hidden in purposefully vulnerable programs or websites.
Nmap is a powerful network scanning tool used to discover hosts and services.
Gobuster is a fast directory and file brute-forcer for web enumeration.
ExifTool is a tool for reading and editing metadata in images and other files.
Hydra is a fast password-cracking tool for various authentication protocols.
Netcat (nc) is a versatile networking tool for reading and writing data over TCP/UDP.